OverTheWire Leviathan – Level 3

Again, by reviewing the dynamic library calls of the SETUID ELF, level3, found within user leviathan3‘s home directory, we can observe another strcmp() call comparing the inputted password to the accepted value.
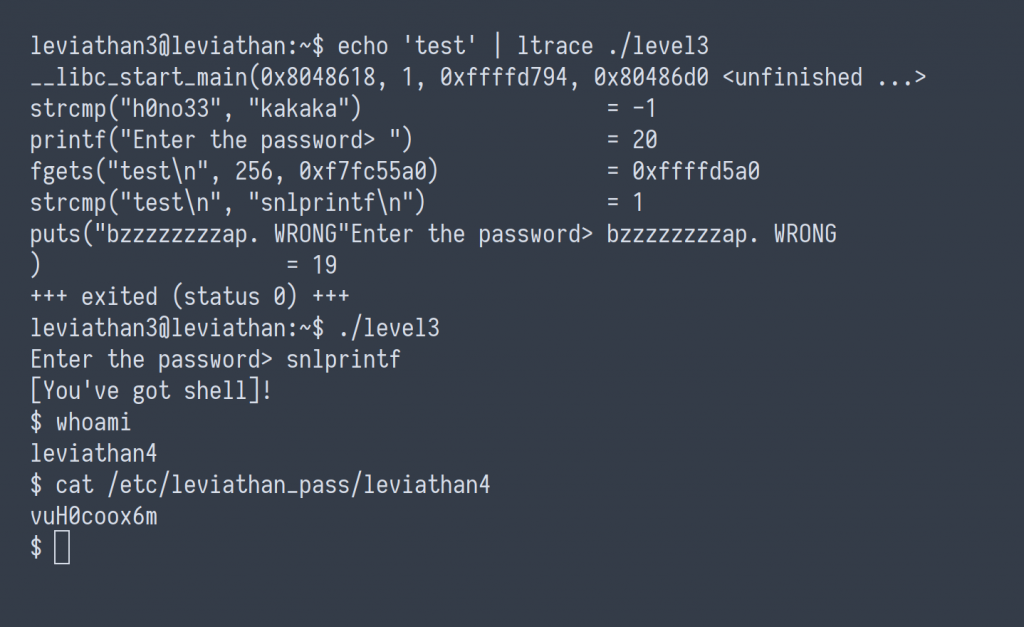
leviathan4 : vuH0coox6m